We have received reports of ransomware that is being distributed via an Excel attachment to an e-mail message. This specific ransomware is a variant of Locky and has been dubbed Osiris as it encrypts files with a .osiris extension. For more information on Locky please click here and here.
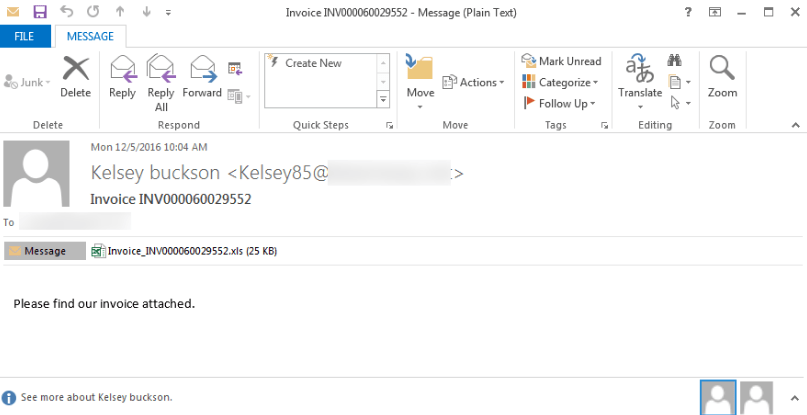
Please be on the look-out for an email message which may appear something like the following:
It has been noted that these ransomware e-mails contain Invoice INV[random numbers] in the Subject line of the message, and contain a zip attachment with a name Invoice_INV[random numbers].xls.
If the attachment is opened the user will see a blank spreadsheet and will be prompted to enable macros. If the user enables the macros, ransomware will install via renamed DLL files.
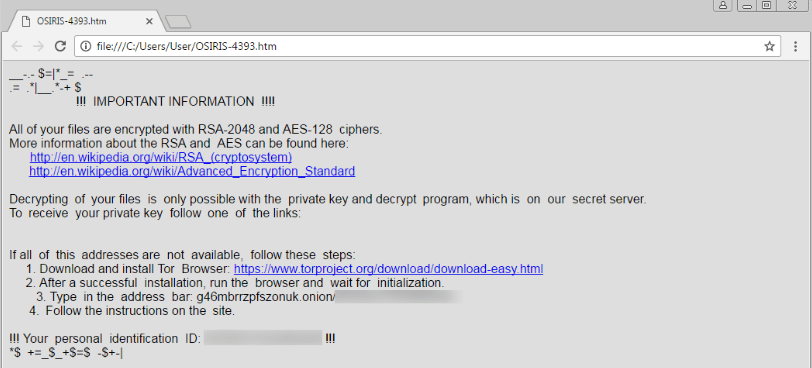
Once activated, Locky will begin scanning the device and any connected devices, systems or file shares for certain file types, and will begin scrambling file names and encrypting them with .osiris extensions. A ransom note, like the following will appear following the completion of file encryption:
If you receive an e-mail like the one shown above, or if you see .osiris files appearing on your device(s) or network shares, you should contact the NYU IT Service Desk immediately at 212.998.3333 or at AskIT@nyu.edu and disconnect your computer from the network. System Administrators who see .osiris files appearing on their network shares should lock these Active Directory users and computer accounts.
The best way to handle this type of ransomware infection is to restore from back-ups following a wipe of the infected device. It is recommended that you check any files synced with with services such as NYU Box, DropBox, or Google Drive prior to restoration to ensure that these files have not been infected. Following restoration from back-ups, please be sure to disconnect back-up devices.
For more information on Locky/Osiris, please see: https://www.bleepingcomputer.com/news/security/locky-ransomware-switches-to-egyptian-mythology-with-the-osiris-extension/