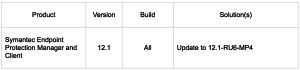
We recommend that you update your install of Symantec Endpoint Protection (anti-virus software) to the recent version (March 2016 update, 12.1.6). This update address the security vulnerabilities detailed below. To install the updated version of Symantec, please visit: https://home.nyu.edu, and click Ask NYU IT. The Symantec update will be available in the Software section at the top left of the screen.
(click images to enlarge)
_ _ _ _ _ _ _ _ _ _ _ _ _
Security Advisories Relating to Symantec Products – Symantec Endpoint Protection Multiple Security Issues
Revisions
None
Severity
Overview
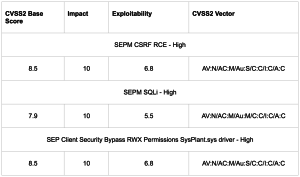
Symantec Endpoint Protection (SEP) was susceptible to a number of security findings that could potentially result in an authorized but less privileged user gaining elevated access to the Management Console. SEP Client security mitigations can potentially be bypassed allowing arbitrary code execution on a targeted client.
Details
The management console for SEPM contained a cross-site request forgery vulnerability that was the result of an insufficient security check in SEPM. An authorized but less-privileged user could potentially include arbitrary code in authorized logging scripts. When submitted to SEPM, successful execution could possibly result in the user gaining unauthorized elevated access to the SEPM management console with application privileges.
There was a SQL injection found in SEPM that could have allowed an authorized but less-privileged SEPM operator to potentially elevate access to administrative level on the application.
The sysplant driver is loaded as part of the Application and Device Control (ADC) component on a SEP client if ADC is installed and enabled on the client. A previous security update to this driver did not sufficiently validate or protect against external input. Successfully bypassing security controls could potentially result in targeted arbitrary code execution on a client system with logged-on user privileges. Exploitation attempts of this type generally use known methods of trust exploitation requiring enticing a currently authenticated user to access a malicious link or open a malicious document in a context such as a website or in an email.
NOTE: Customers not using ADC are not impacted by the client issue, CVE-2015-8154.
Symantec Response
Symantec product engineers have addressed these issues in SEP 12.1-RU6-MP4. Customers should update to RU6-MP4 as soon as possible to address these issues.
Symantec is not aware of exploitation of or adverse customer impact from this issue.
Update Information
Symantec Endpoint Protection Manager 12.1-RU6-MP4 is available from Symantec File Connect.
Best Practices
As part of normal best practices, Symantec strongly recommends the following:
- Restrict access to administrative or management systems to authorized privileged users.
- Restrict remote access, if required, to trusted/authorized systems only.
- Run under the principle of least privilege where possible to limit the impact of potential exploit.
- Keep all operating systems and applications current with vendor patches.
- Follow a multi-layered approach to security. At a minimum, run both firewall and anti-malware applications to provide multiple points of detection and protection to both inbound and outbound threats.
- Deploy network- and host-based intrusion detection systems to monitor network traffic for signs of anomalous or suspicious activity. This may aid in the detection of attacks or malicious activity related to the exploitation of latent vulnerabilities.
Credit
Symantec would like to thank Anatoly Katyushin with Kaspersky Labs https://www.kaspersky.com, for finding and reporting CVE-2015-8152, CVE-2015-8153 and working closely with Symantec as they were addressed.
Symantec would like to thank enSilo Research Team, https://www.ensilo.com, for reporting CVE-2015-8154 and working closely with Symantec as it was addressed.
References
CVE: These issues are candidates for inclusion in the CVE list (http://cve.mitre.org/cve), which standardizes identifiers for security problems.
BID: Symantec SecurityFocus, http://www.securityfocus.com, has assigned Bugtraq IDs (BIDs) to these issues for inclusion in the Security Focus vulnerability database.
Symantec takes the security and proper functionality of our products very seriously. As founding members of the Organization for Internet Safety (OISafety), Symantec supports and follows responsible disclosure guidelines . See the Organization for Internet Safety Guidelines for Security Vulnerability Reporting and Response (PDF).
Please contact secure@symantec.com if you feel you have discovered a security issue in a Symantec product. A member of the Symantec Product Security team will contact you regarding your submission to coordinate any required response. Symantec strongly recommends using encrypted email for reporting vulnerability information to secure@symantec.com. The Symantec Product Security PGP key can be found at the location below.
Symantec has developed a Product Vulnerability Response document outlining the process we follow in addressing suspected vulnerabilities in our products. This document is available below.
Copyright (c) 2016 by Symantec Corp.
Permission to redistribute this alert electronically is granted as long as it is not edited in any way unless authorized by Symantec Product Security. Reprinting the whole or part of this alert in any medium other than electronically requires permission from secure@symantec.com
Disclaimer
The information in the advisory is believed to be accurate at the time of publishing based on currently available information. Use of the information constitutes acceptance for use in an AS IS condition. There are no warranties with regard to this information. Neither the author nor the publisher accepts any liability for any direct, indirect, or consequential loss or damage arising from use of, or reliance on, this information.
Symantec, Symantec products, Symantec Product Security, and secure@symantec.com are registered trademarks of Symantec Corp. and/or affiliated companies in the United States and other countries. All other registered and unregistered trademarks represented in this document are the sole property of their respective companies/owners.