We’ve received reports of several Multi Factor Authentication (MFA) related phishing attempts, and as an update to the following blog post on the subject, we would like to take the opportunity to remind everyone that scammers are using the following methods to exploit MFA and thereby gain access to accounts and systems.
- User credential compromise a/k/a credential theft, accomplished when:
- Scammers steal MFA codes and user credentials by luring victims to malicious websites. This is often accomplished via phishing messages directing users to a malicious web page, which presents users with a spoofed login prompt designed to steal their credentials and MFA codes. Once scammers obtain this information, they’ll attempt a takeover of an account by changing the account password and the device registration (unregistering your device and registering theirs).
- Passwords are cracked due to the use of weak passwords or passphrases, which gives scammers the ability to “MFA bomb” users with push notification requests until they accept a request just to stop the notifications, thereby giving scammers access to their account.
- Malware such as spyware in which credentials and generated MFA codes are stolen from hacked devices, e.g., MFA codes are generated by the user and sent to SMS text messages applications.
- Passcodes from the Duo app or the Help Desk are intercepted by the scammer.
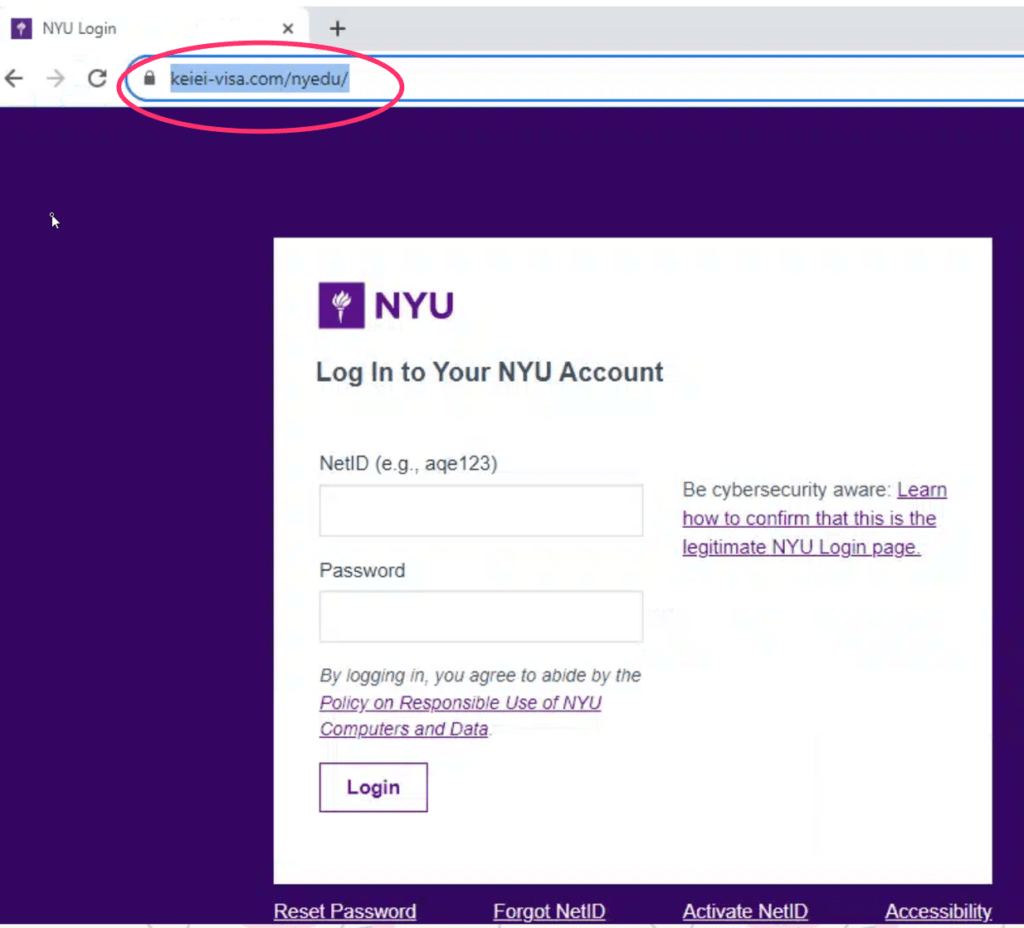
The following is an example of a spoofed prompt on a malicious web page. Note that the telltale sign of a malicious website/page is the URL, which in this case, is not what you’d expect to see at an NYU login prompt.
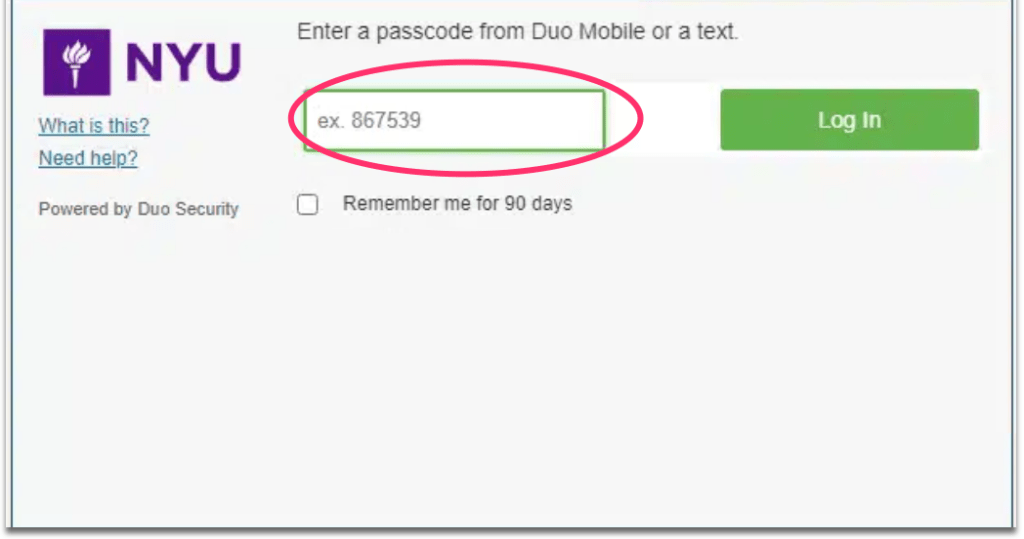
The user enters their credentials into the above-shown spoofed prompt, and then enters an MFA passcode into the spoofed prompt below.
As stated above, once credentials & a code is entered into malicious pages, scammers steal the information and attempt an account takeover.
What you can do:
- Use strong (14+ character) and unique (to each account) passwords or passphrases.
- Never share or reuse your credentials
- Use a well reviewed and rated password manager which is compatible with your devices to manage your many passwords/passphrases..
- Remember, IT Support will never call you and request your credentials or ask that you accept an MFA prompt.
- If you suspect your account credentials may have been compromised, change them immediately.
- Only download from trusted sources like Apple’s App Store or Google Play.
- Use antivirus software on your devices.
- Always confirm you are in the expected website by reviewing the website’s URL in your browser’s address bar.
- Only visit websites by typing trusted URLs into your browser’s address bar or using a trusted link that you have bookmarked.
- Only connect to trusted password protected public Wi-Fi, and use VPN, which protec ts your internet traffic in transit.
- For questions regarding phishing, or to report phishing please email phishing@nyu.edu.
- To report a security incident, please email security@nyu.edu.
- Remember not to authorize MFA requests you have not made. If you receive an authentication request you did not initiate, select DENY on the Duo screen. You will then be asked: “Was this a suspicious login?” Select Yes, and Duo administrators will be alerted.
- Each browser has a separate Duo session request.
- If you’ve inadvertently authorized a request, confirm that there are no unauthorized devices that are registered to your account as follows: