Please be advised of an exploit requiring no user interaction, which affects Cisco Jabber for Windows in which XMPP messaging services are enabled. Systems using Cisco Jabber in phone-only mode (without XMPP messaging services enabled) are not vulnerable to the exploit and Cisco additionally advises that the vulnerability is not a threat when Cisco Jabber is configured to use messaging services other than XMPP messaging.
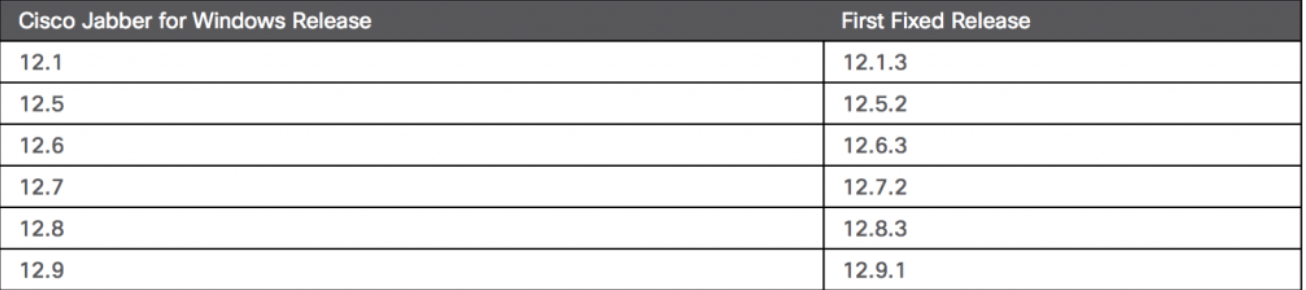
This vulnerability impacts Cisco Jabber 12.1 – 12.9 and is being tracked as CVE 2020 3495, with a severity score of 9.9/10, and allows for remote code execution with the privileges of the targeted user. Users are advised to update immediately. The following is a table which contains the corresponding update for each release.
Image courtesy of CISCO
Please note that this vulnerability does not affect Jabber for MacOS or mobile platforms.
Resources:
- https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-jabber-UyTKCPGg
- https://threatpost.com/attackers-can-exploit-critical-cisco-jabber-flaw-with-one-message/158942/
- https://www.zdnet.com/article/cisco-warns-jabber-im-client-for-windows-has-a-critical-flaw/