There has been a recent uptick noted in the delivery of phishing via SMS text messages (a/k/a “SMiShing”) in the form “URL padding” or the front loading of a web address of a malicious site with a legitimate domain name. The goal of these attacks is credential stealing as users are prompted to enter their credentials in phishing pages to which they are directed.
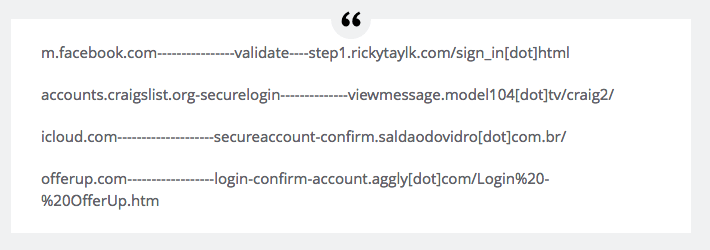
Specifically, the true site domains are concealed, as the subdomain addresses are padded with enough hyphens to push the true link destinations out of view. Another reason these attacks have been successful is with SMS messages, it is not possible to confirm the legitimacy of a site before clicking it, and upon arrival at the site, the URL padding masks the true site address.
Please see the following examples of URL padding:
(Image courtesy of Ars Technica)
The phishing pages are hosted on sites with legitimate domain names that have been compromised.
It is recommended that whenever possible you avoid clicking links that have been transmitted by SMS messages, and that you do not click links with hyphens (URL padding or front loading) as shown above. If you visit a web page in which the URL appears to be front loaded, it’s likely a phishing page, and we recommend that you close the browser tab containing the page or exit the browser as it’s important to avoid clicking any elements on a possibly malicious web page or pop-up.