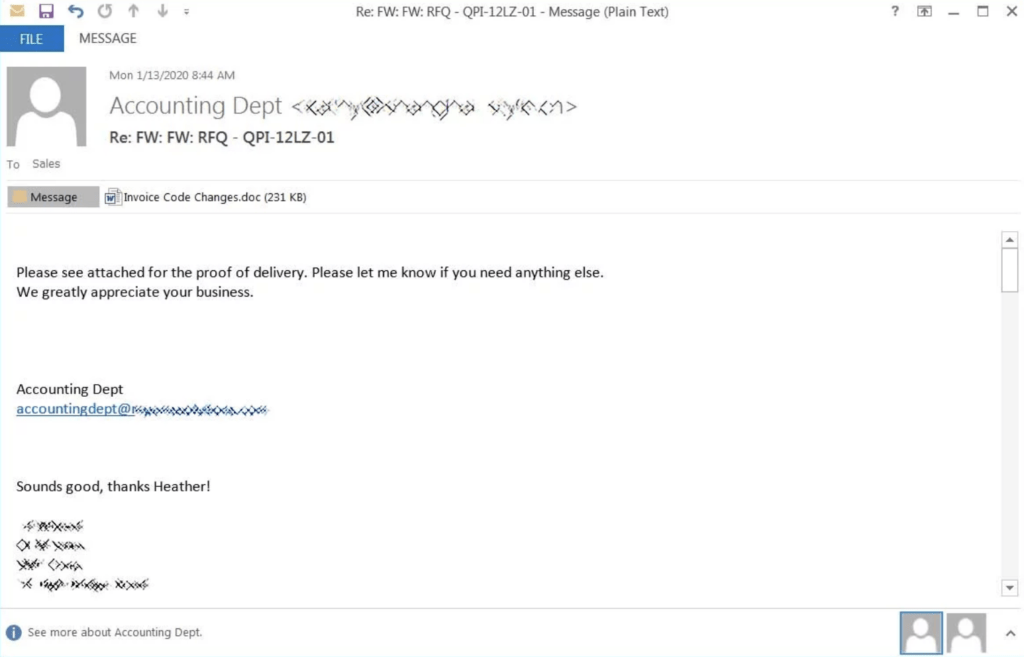
Current phishing campaigns delivering both Emotet and Trickbot malware are emails containing embedded links or attaching documents, including, proof-of-delivery documents, reports, agreements and statements. The following is an example of an email from this campaign:
Image courtesy of BleepingComputer
In all known campaigns, recipients receive the following message when they open the associated attachment or click the embedded link “document only available for desktop or laptop versions of Microsoft Office Word”. Recipients are presented with a choice of either “Enable Editing” or “Enable Content” in order to view the document. When the document opens, malicious macros run the Emotet trojan, which will use an infected device to send out malicious spam. Emotet will also install the Trickbot trojan which can be used to compromise a network and the devices on it, which may lead to a Ryuk ransomware infection.
Please be reminded of the following:
- Never open attachments or click embedded links in unexpected email messages. When in doubt, confirm legitimacy with the sender using a trusted means of communication, such as a phone number you look up.
- Avoid enabling macros/content in attachments from known/unknown senders absent a known legitimate reason.
- Use NYU sponsored anti-malware protection on all desktops and laptops connecting to NYU’s network. For more information on access and eligibility, see www.nyu.edu/it/malware-protection