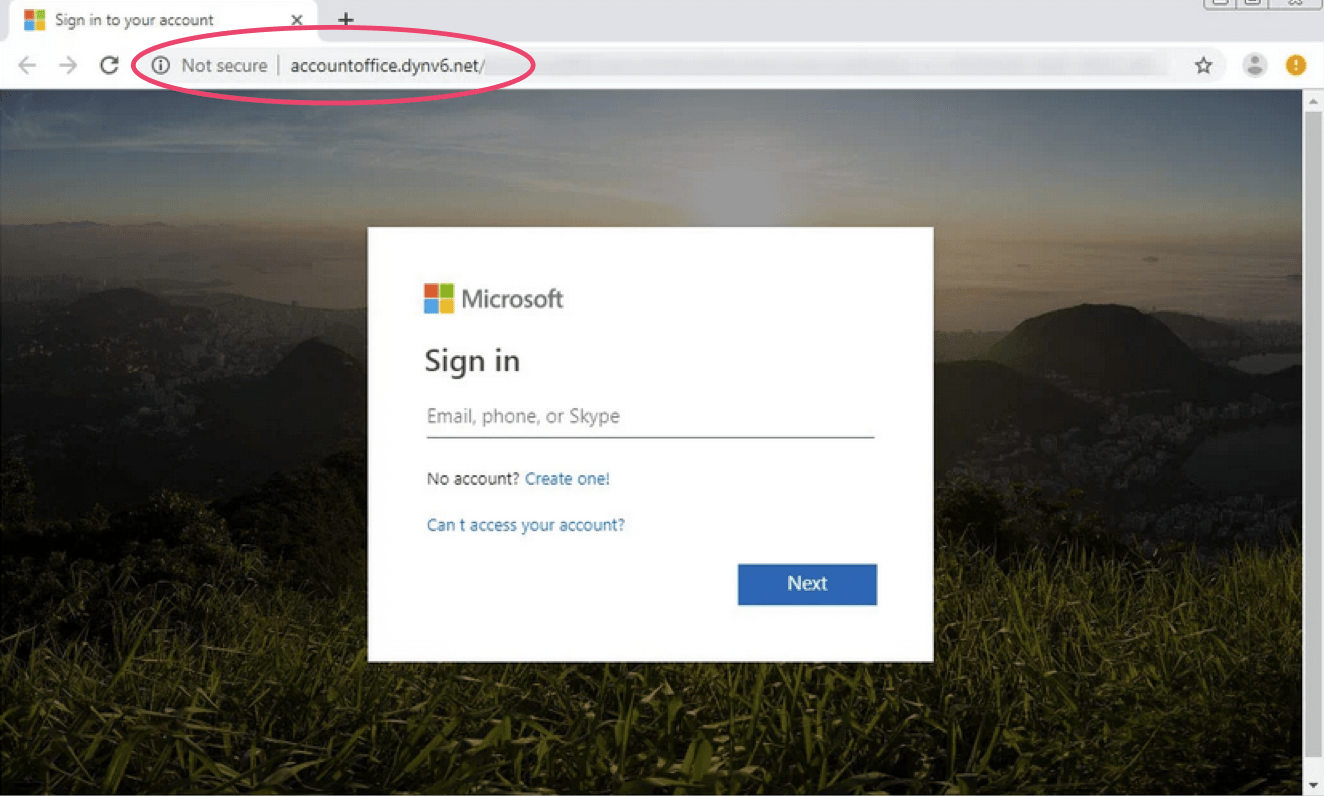
Please be advised that “Unusual sign-in activity” email alerts purporting to be from Microsoft are being used to steal user credentials. Emails in this campaign tend to look almost identical to legitimate Microsoft alerts and even use the same legitimate sender address: “account-security-noreply@accountprotection.microsoft.com”. What differs is what occurs when you click the “Review recent activity” link in the phishing message. Instead of being taken to a view of your recent account activity, you are brought to a spoofed Microsoft landing page with a login prompt as follows:
Image courtesy of BleepingComputer
If credentials are entered in the spoofed login prompt, they are stolen/compromised and users are then redirected to a legitimate Microsoft webpage saying “We’re unable to complete your request”.
Please be reminded of the following:
- sender email addresses can be spoofed, and are not an indicator that an email is legitimate.
- be sure to view the URLs associated with landing pages. In this phishing campaign the URL associated with the landing page, “accountoffice.dnyv6.net”, is the “phishing tell”.
- If you suspect your credentials have been compromised, it is recommended that you change your password asap.