The Office of Information Security (“OIS”) has been made aware of a phishing campaign dubbed “Silent Librarian” that is targeting the NYU community. This phishing campaign is designed to steal login credentials, and has been targeting universities, companies and government agencies around the world. Silent Librarian has targeted more than 300 universities in 22 countries, and the cost to universities alone is estimated to be around 3.4 billion.
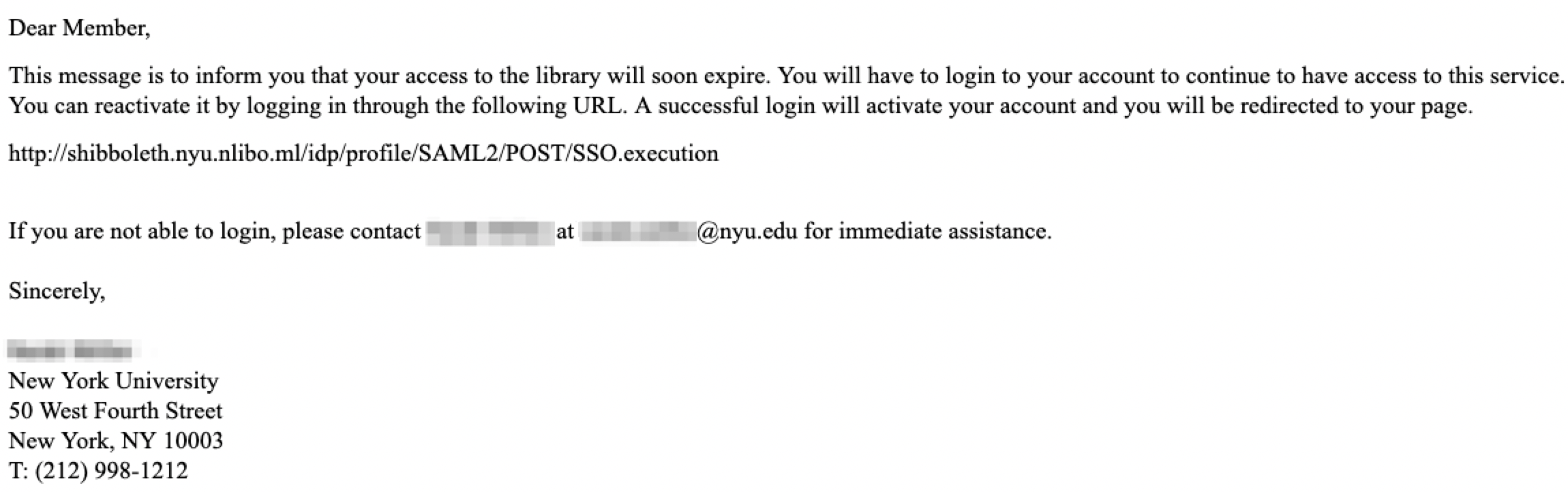
The following is an example of a Silent Librarian phishing message.
Please note that these phishing messages often arrive from spoofed sender email addresses, and appear to be signed by actual Library personnel. The subject lines of these messages have remained consistent over time and tend to be “Library Account”, “Library Notifications”, or “Library Services” with the name of the university sometimes appended to the subject. The phishing ‘tells’ in this email message are the incorrect library address, and the embedded link, which takes users to a spoofed login prompt. Although the embedded link contains familiar elements, please be reminded to look for “https://shibboleth.nyu.edu” in the typed link, link preview and in your browser’s address bar once you’ve clicked a link.
Further, because links can be spoofed (the destination URL is not the same as the typed URL), the following are recommended best practices:
- Never click embedded links or open attachments in unexpected email.
- When in doubt of the legitimacy of an email message, contact the sender using a trusted means of communication, such as the sender’s NYU Directory phone number.
If you have fallen for this phishing campaign, please change your NetId password asap via: https://start.nyu.edu/.
Resources:
- https://info.phishlabs.com/blog/silent-librarian-more-to-the-story-of-the-iranian-mabna-institute-indictment
- Previewing URLs, http://www.nyu.edu/servicelink/KB0017304