NYU IT has been notified by Homeland Security about an emerging ransomware email threat (a new strand of Petya) occurring in many countries around the world, and NYU’s Office of Information Security is actively monitoring for any impact at NYU. Ransomware is a type of malicious software that infects a computer and restricts users’ access to the infected machine, including any attached storage until a ransom is paid to unlock it. Individuals and organizations are discouraged from paying the ransom, as this does not guarantee that access will be restored. Using unpatched and unsupported software may increase the risk of proliferation of cyber security threats, such as ransomware.
Phishing Alert: We advise you to treat unknown senders of email with vigilance and to not click on URLs in emails, without checking the actual URL (hover over the URL and check if it is going to the correct location).
Patching Alert: Please keep all systems up to date, with the latest security and software patches.
Anti-Virus Alert: Please update your Anti-Virus software to the latest version.
The following websites provide additional information:
https://krebsonsecurity.com/2017/06/petya-ransomware-outbreak-goes-global/
If you require assistance or for urgent IT issues and security escalations, contact the IT Service Desk (24×7) at 212-998-3333 or email AskIT@nyu.edu.
This information will be available on the NYU IT Security News blog at: https://wp.nyu.edu/itsecurity/
For NYU IT Security information, see: https://www.nyu.edu/it/security
Additional Information:
This ransomware has been reportedly spreading globally via a malicious email attachment. Petya is spreading using the same propagation method (a hacking tool called “EternalBlue”) as the WannaCry ransomware attack last month. For more information on WannaCry, please click here and here. Petya does not encrypt individual files, rather it targets a computer’s master boot record and is aimed at a computer’s entire file system. Data is being held hostage pending receipt of a Bitcoin payment of $300. Please be reminded that payment of a ransom does not guarantee receipt of the decryption key or the successful restoration of data.
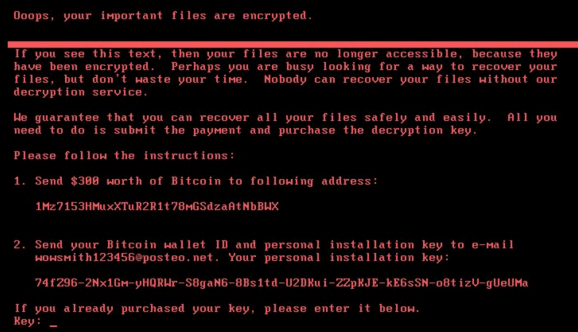
The following is the message that displays on the screens of MicroSoft Windows devices which have been infected with Petya:
(Image courtesy of KrebsonSecurity)
Researchers report that this ransomware is using a modified version of EternalBlue to get inside the network (once the ransomware has been activated), and the PSExec command line tool to spread the ransomware from machine to machine. It is not yet clear if Petya mimics the worm capability of WannaCry and can spread between computers without user interaction.
For system administrators, it is recommended that the latest Microsoft patches be applied especially patch MS17-010.
Please be reminded that if you suspect a ransomware attack:
- Disconnect from the network and any file shares.
- Contact the IT Service Desk (24×7) at 212-998-3333 or email AskIT@nyu.edu.
- Wipe your device.
- Recover files from a backup or synch performed prior to the encryption.
- Disconnect backups by disconnecting backup devices or disconnecting from file sharing services.
For more information, please see:
https://arstechnica.com/security/2017/06/a-new-ransomware-outbreak-similar-to-wcry-is-shutting-down-computers-worldwide/
https://researchcenter.paloaltonetworks.com/2017/06/unit42-threat-brief-petya-ransomware/