Please be advised that Microsoft plans to release an update for a critical Word flaw today, as part of Patch Tuesday. It is recommended that this patch is applied as soon as it becomes available. This vulnerability allows the installation of malware, in this case a banking trojan dubbed Dridex, when a target/user opens a maliciously-crafted MS Word email attachment. This vulnerability is known to affect all Windows versions of Word. The exploit has not been proven or disproven to work on Mac versions of Word.
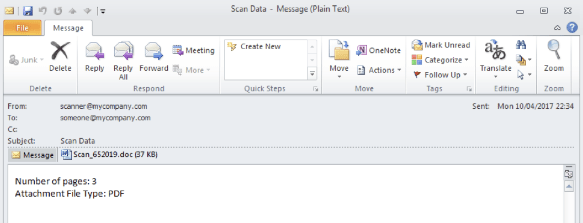
Dridex infused Word documents typically arrive as Rich Text Format (RTF) attachments to emails purporting to be from from “device”, “copier” “documents”, “no-reply” or “scanner”. In all known cases, the subject line of the emails reads “Scan Data”. Opening the documents attached to these emails will install a Dridex bot on your system that is known to capture banking information. It has been observed that this exploit does not execute when the document is viewed in a Microsoft view known as “Protected View”, which is a read-only mode in which most editing functions are disabled. However, if you opt to print the document or “Enable Editing” in Protected View, the exploit will run.
A sample Dridex email is shown below:
For more information, please see: