For Staff, Faculty and Students running personal or departmental installations of WordPress:
If you have not already done so, it is critical that you upgrade to WordPress version 4.7.2, which was released on 1/26/17. This upgrade fixes a bug (in the REST API) allowing hackers to bypass authentication systems and edit the titles and content of WordPress pages. The web security firm WordFence reports that over 1.5 million WordPress pages have been defaced by 20 hacking groups. 800,000 sites have been defaced in the last 48 hours alone.
For people using NYU’s central version of WordPress on http://wp.nyu.edu, the version is already up to date, and you do not need to take additional action.
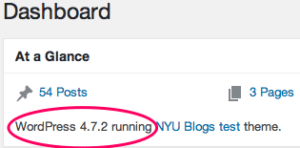
You can confirm the version of WordPress that you are running in the administrative view. The Dashboard view will display the version running as follows:
If you are not running NYU’s central version of WordPress, and have questions concerning the version you are running or upgrading to version 4.7.2, please consult your local tech support.
For more information, please see:
1) https://www.bleepingcomputer.com/news/security/attacks-on-wordpress-sites-intensify-as-hackers-deface-over-1-5-million-pages/
2) http://www.welivesecurity.com/2017/02/08/100000-wordpress-webpages-defaced-recently-patched-vulnerability-exploited/