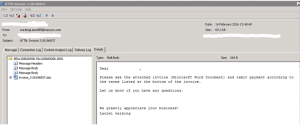
Ransomware dubbed “Locky” is spreading via email, in the form of a Word file attached to e-mail messages. Locky email is translated to various languages and localized by region. E-mails with this type of ransomware may look something like (*click images to enlarge):
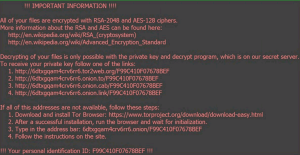
Once the Word attachment is opened, users see scrambled content and are asked to enable macros. When/if macros are enabled, the malware spreads, and encrypts nearly all file formats as hash.locky files including any mounted USB sticks and network file shares. Once encrypted, users receive the following:
Locky ransomware typically asks victims to pay between 0.5 and 2 Bitcoins ($208 – $800) for the decryption key.
The antivirus software available thru NYU, Symantec Endpoint Protection, may not provide full protection against all variants of this malware. Google also checks for viruses, and you can see if one has been identified. If so, the Gmail attachment will have “virus found”, as in the image below:
Therefore, if you see .locky extension files appearing on your computer, USB drives, or network shares, you should contact the NYU IT Service Desk immediately at 212.998.3333 or at AskIT@nyu.edu and disconnect the computer from the network. System Administrators who see .locky extension files appearing on their network shares, may look up the file owner on _Locky_recover_instructions.txt file in each folder. It is recommended that you lock these Active Directory user and computer accounts.
The best way to handle such an infection is to restore back-ups from external hard-drives or USB devices. You must wipe the machines before mounting back-up devices, and it is recommended that you check any files synched with services such as NYU Box, DropBox or Google Drive to ensure that these files have not been infected.