This week we were tasked with practicing packet sniffing.
I used the free, open-source software WireShark . For this exercise, I ran in on my computer while logged into the NYU network, and I wasn’t using my laptop at the time, so I only sniffed 459 packets.
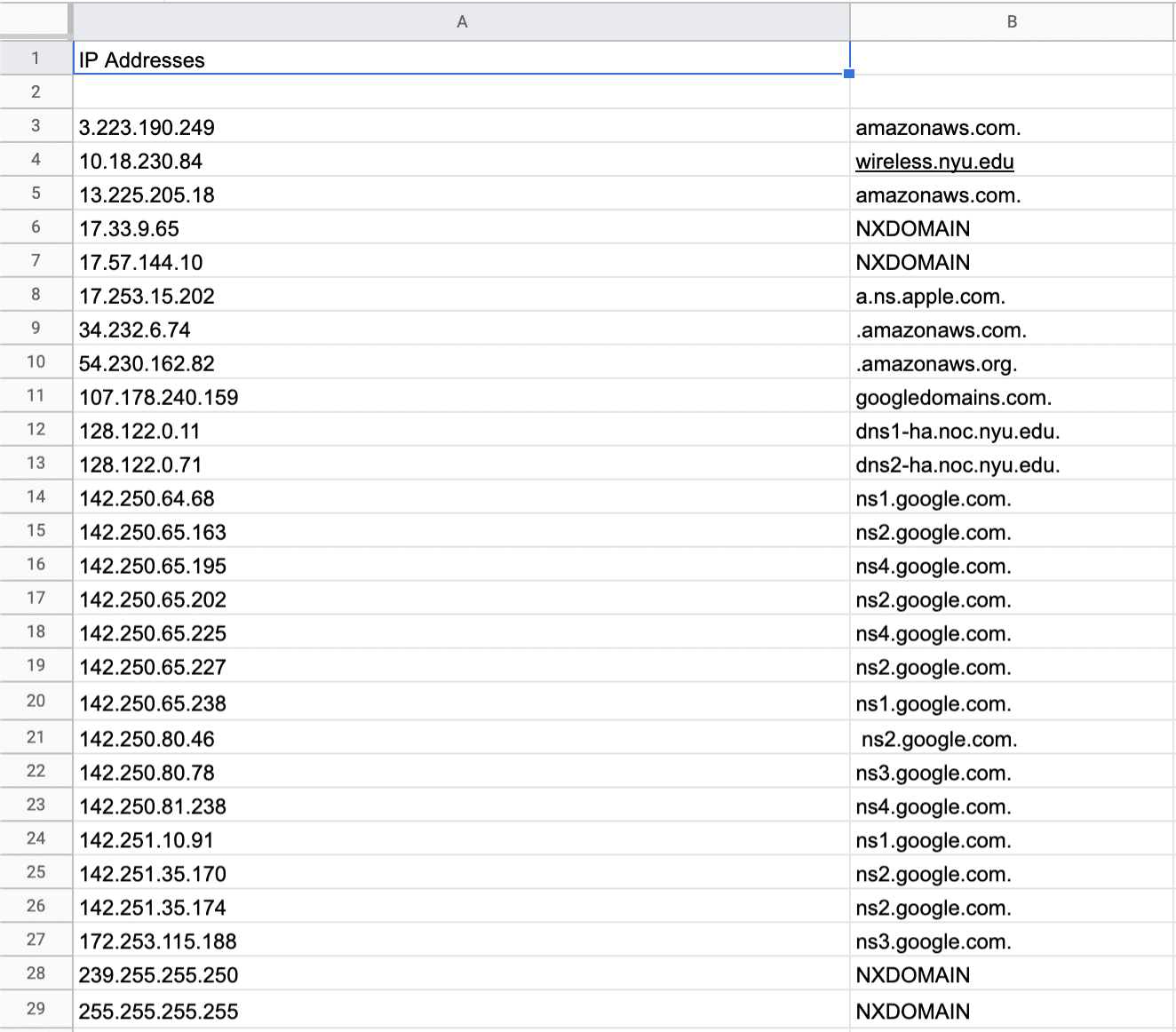
I thought it would be interesting to take all the HTTP data and run the IP addresses through NS Lookup on my terminal. I wanted to see the companies that my information was traveling through. To do this, I filtered by HTTP and downloaded the data to a CSV file, and I then uploaded it to google sheets and isolated the IP address.
I noticed that most of my information was going through either amazon web services or google.
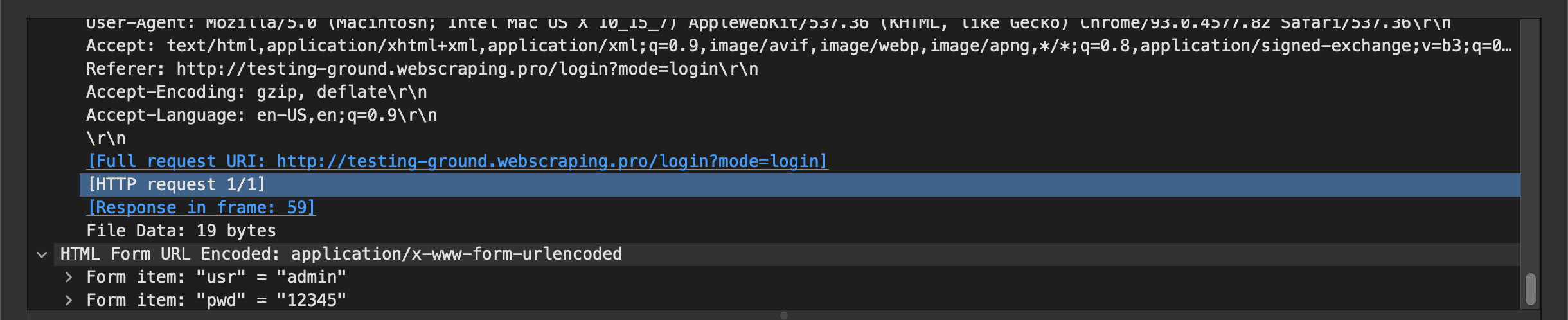
Next, I ran a tutorial on WireShark that allowed me to test a nonsecure HTTP website. You can see below that I was able to find both the user name and password. It’s fascinating how easily I was able to get that information and just how vital HTTPS is.